Robust Wireless Communications
Wireless communications are subject to various types of noise and interference, and several decades of research has produced reasonably effective approaches to communicate in a variety of settings. However, the vast majority of these approaches are not designed to manage intentional interference, especially in the form of jamming attacks. Moreover, the approaches that address jamming attacks consider only simplified attack models. In our work, we aim to advance both the attack models of interest and the techniques used to defend against these attacks. We have shown that modern software-defined radios introduce significant gains for both attackers and defenders, in particular allowing for on-the-fly adaptation of radio software and parameters to provide reactive defense and proactive evasion of threats.
Understanding Next-Generation Jamming Attacks
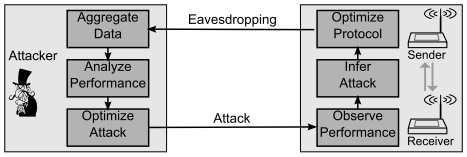
Understanding and modeling jamming attacks has long been a problem of interest in wireless communication and radar systems. In wireless ad hoc, mesh, and sensor networks using multi-hop communication, the effects of jamming at the physical layer resonate into the higher layer protocols, for example by increasing collisions and contention at the MAC layer, interfering with route discovery at the network layer, increasing latency and impacting rate control at the transport layer, and halting or freezing at the application layer. Adversaries that are aware of higher-layer functionality can leverage any available information to improve the impact or reduce the resource requirement for attack success. For example, jammers can synchronize their attacks with MAC protocol steps, focus attacks in specific geographic locations, or target packets from specific applications. Moreover, these same offensive techniques can be used to defend against other threats.
Related Publications
Efficient Defense and Mitigation of Jamming Attacks
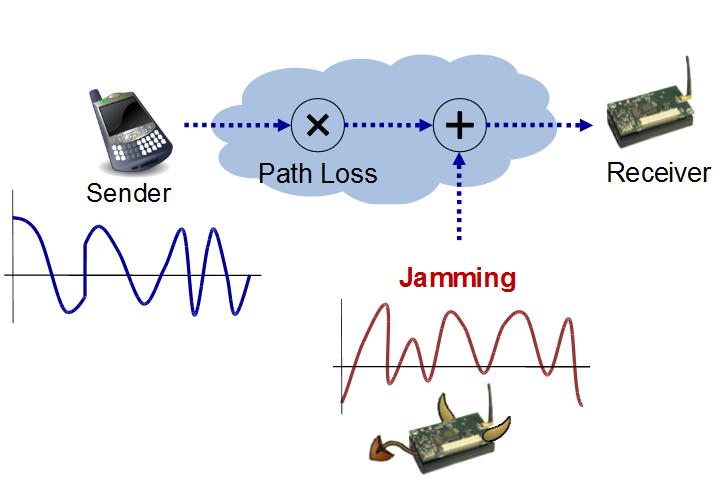
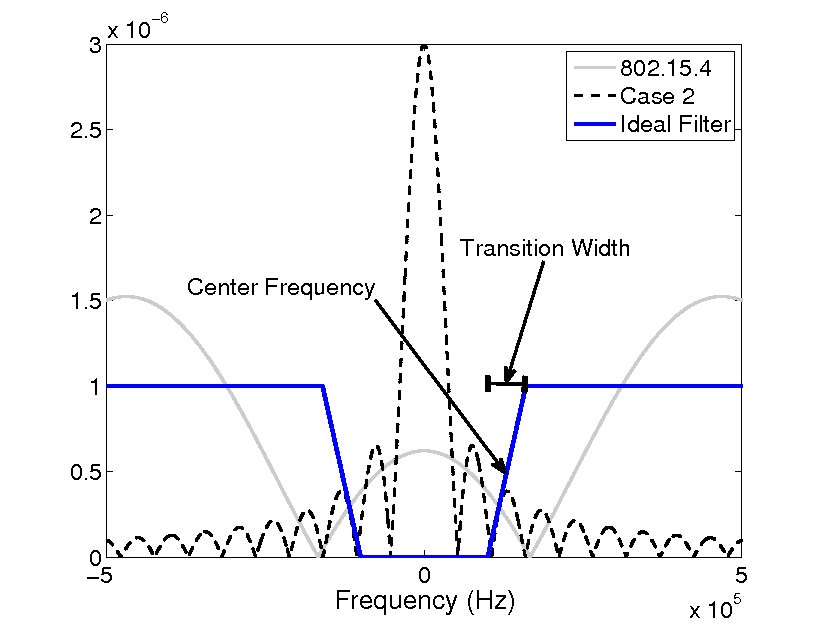
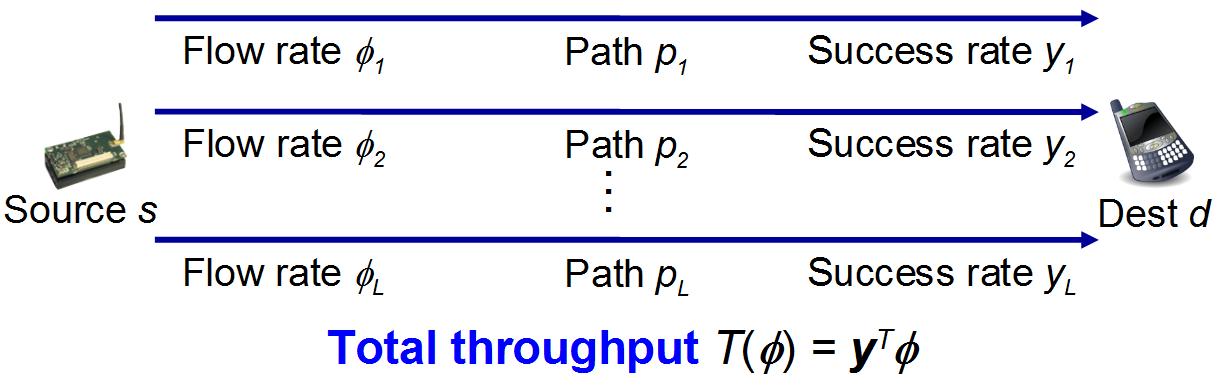
The introduction of software-defined radios into the marketplace allows for new types of software-defined signal processing, communication, and networking techniques to assist in mitigating jamming attacks in a variety of ways. Such approaches often involve the use of cross-layer information to correctly diagnose and repair the protocol stack or to share information and signals through network interfaces. We have studied the use of software filtering mechanisms to identify and eliminate jamming signal at the receiver without obliterating the desired signal, and we have demonstrated the value of such approaches in an SDR testbed implementation. In addition, we have developed cross-layer protocol modifications that use higher-layer indicators of network failure in cases where the attacks cannot be explicitly detected. Toward this end, we have shown that multi-channel communication, multi-path routing, and adaptive transport protocols can be employed to achieve a level of diversity that aids in mitigating jamming attacks, even when jammers are mobile and relatively stealthy.
Related Publications
Modeling Interactions between Attackers and Defenders
As described above, new software-defined radio and network capabilities allow attacking, greedy, or defending opponents to adapt their protocol operations or behaviors in reponse to detected threats or failures, or even proactively in a sort of moving target defense technique. The value of such adaptation is often clearly understood as long as the opponent is static, as convergencen properties can be well-defined in such a case. However, if multiple opponents are simultaneously adapting in response to each other, the system dynamics can not be as easily described. We thus aim to model such multi-player adaptation using a combination of game theory, control theory, empirical data analytics, and stochastic modeling.