Secure and Resilient Networking
Wireless networking enables flexible and cost-effective deployment of communication systems to support numerous applications, from traditional data services to vehicular safety management to critical infrastructure support (e.g., the Smart Grid). In many of these systems, the timely delivery of data and control messages can be as or more important than the confidentiality or integrity of the messages themselves, so traditional cryptographic approaches are often insufficient to provide the desired guarantees. In such scenarios, network redundancy in the form of multiple paths or the ability to re-organize network assets and resources becomes crucial, especially in highly dynamic or failure prone networking scenarios. Toward these goals, we have been developing a suite of algorithms/protocols spanning multiple layers of the network protocol stack (layers 2 through 4) to provide recovery capabilities and resilience to failures, outages, misbehavior, large scale disasters, and cascading effects of errors and attacks at lower layers.
Secure and Resilient Networking and Data Transport
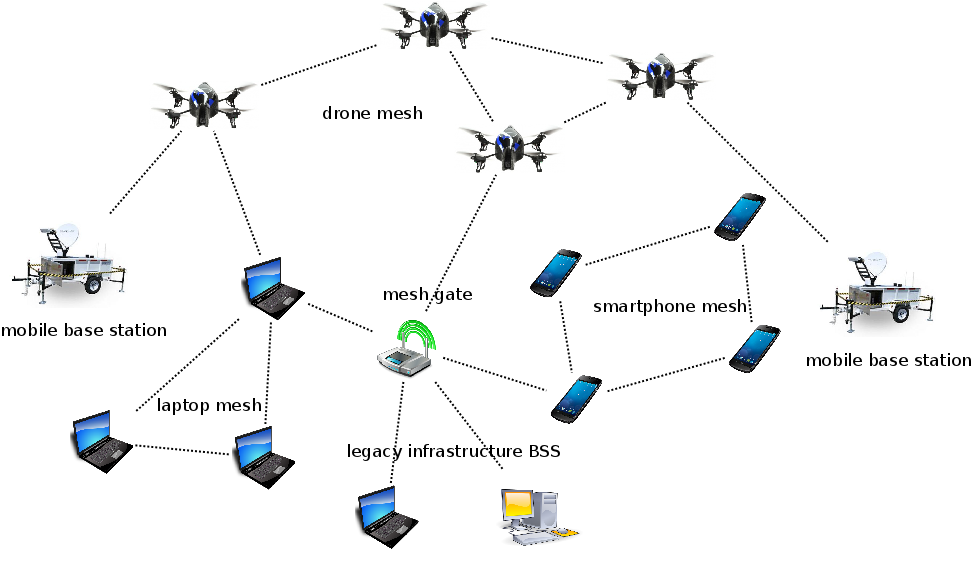
Wireless networks enable flexible deployment, and wireless meshes enhance this flexibility by further eliminating the need for complete coverage by access points or base stations. Wireless meshes offer additional resilience in the form of path redundancy and diversity, providing stronger protections against network failure or denial-of-service. This resilience therefore enables support for unique applications and capabilities for emergency/disaster communication, underserved areas, or to provide cellular offload. We are developing an integrated architecture for heterogeneous mesh protocols and mesh nodes to form one unified mesh system to seamlessly support a wide variety of applications and usage scenarios, even in the face of mobility, malicious and selfish behavior, or strong (and potentially dynamic) policies on security, privacy, and anonymity. In this new architecture, we are investigating a variety of threats and issues in an effort to design a suite of protocols to provide end-to-end resilience and security.
Related Publications
Security and Privacy in Sensor-Actuator Networks
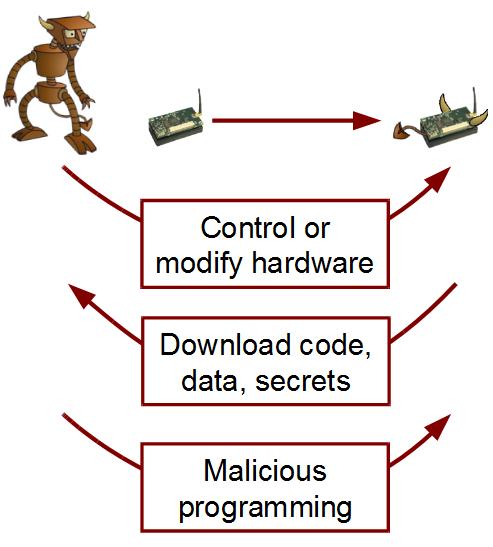
The deployment of wireless sensor-actuator networks for physical sensing and control introduces a number of unique challenges, namely due to the cyber-physical implications of sensing and actuation. Moreover, the small form factor, reliance on battery energy, deployment of unattended devices in potentially challenging or harmful environments, and criticality of timely delivery of control signals further complicate any approach to secure the sensing and actuation processes. Recently, sensor-actuator networks have found new applications in vehicular systems, smart environments, and immersive media applications. Each of these domains presents new requirements and challenges to security and privacy, and we are actively investigating many of them.
Related Publications
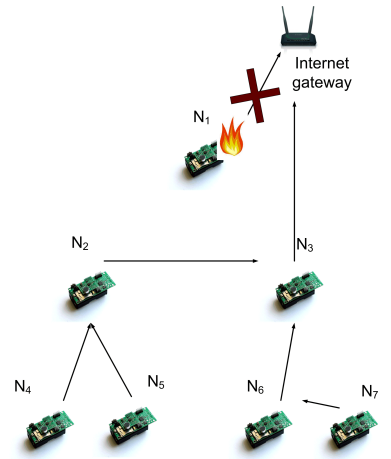
Cross-Layer Self-Organization for Survivable Wireless Networking
Wireless mesh and ad hoc networks are now being proposed for a number of critical data collection and dissemination scenarios, including traditional data and content systems as well as cyber-physical infrastructure (e.g., Smart Grid, Internet of Things). In many of these scenarios, timely delivery of data and control messages can be as critical as the messages themselves, so traditional security mechanisms are insufficient. We thus approach the problem from the network perspective, aiming to provide fast and efficient self-organizing, self-healing, and self-reconfiguring capabilities to allow wireless systems to seamlessly manage and heal themselves. Our approaches rely on cross-layer information sharing to provide efficient and scalable solutions.