Research Tools
We have developed a collection of research tools to assist in demonstration and development of several of our research projects. When possible, we'll make these tools available to the general public via open source licensing. Please contact us for information about getting access to any of the tools that are not posted openly.
Adaptive Jamming and Anti-Jamming Toolbox
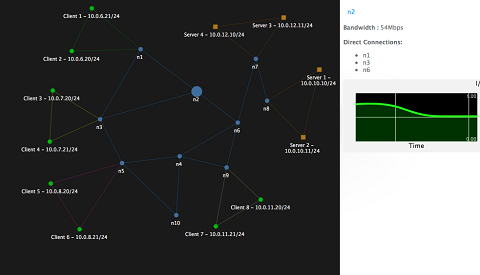
Various adaptive jamming and anti-jamming techniques have been recently proposed by the research community in an effort to provide robust comunication capabilities in the face of dynamic opponents. In order to evaluate and compare these techniques, we have developed a software toolbox as a front-end for a software-defined radio testbed. Our toolbox allows users to visualize and evaluate performance characteristics of a variety of adaptive jamming and anti-jamming techniques.
A description of the work can be found in our Infocom 2012 Demo Abstract. We expect components of this tool to be released under an open-source license in the near future.
Jamming-Resilient Mesh Networking Simulator
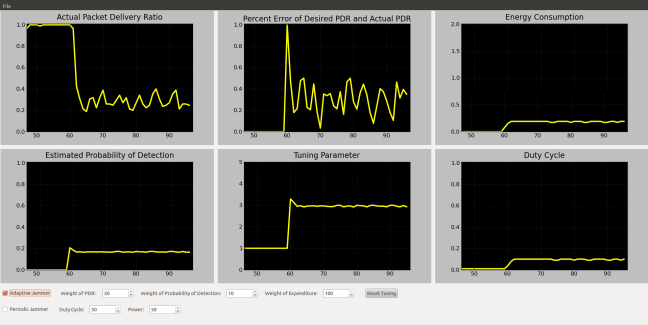
Wireless mesh networks are emerging as the next generation of flexible wireless network architecture, partly due to the ability to self-heal when paths fail or attacks occur. To demonstrate the effects of wireless interference on the most recent mesh standard, IEEE 802.11s, we created a simulator that highlights the path discovery, maintenance, and fault recovery mechanisms of the hybrid wireless mesh protocol (HWMP) defined in 802.11s and how these mechanisms are affected by jamming attacks. We further demonstrate potential modifications to HWMP's path selection protocol that improve resilience to attack and failure.
A description of the work can be found in our Infocom 2012 Demo Abstract. We expect this tool will be released under an open-source license in the near future.
Visualization of Denial-of-Service Attacks and Statistical Detection
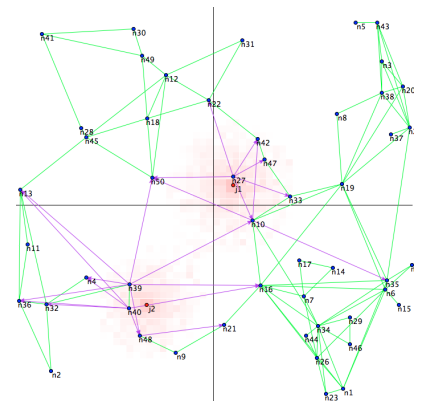
Intrusion detection techniques have been developed for a wide variety of networks and applications. However, in cases where network traffic is encrypted and host identities are hidden from network devices, IDS sensors based on address or identity correlation are inapplicable. Instead of identity-based rules, we have developed a set of rules based solely on network statistics that are observable by network devices even under strict anonymity protections. We have established an emulation and visualization setup using the CORE emulator coupled with an HTML5/Python front end to study a class of network bandwidth consumption attacks and evaluate our real-time detection mechanisms.
A description of the work can be found in our Oakland 2013 Poster Abstract. We expect components of this tool to be released under an open-source license in the near future.